Hello and welcome to the first episode of Eight Weeks of the Essential Eight.
Topic Areas:
- What is the Essential Eight?
- Do I need to implement the essential eight?
- Why the essential eight?
- The Essential 8 Maturity Model
- Targeting a Maturity Level
History of the Essential Eight:
So lets start with a brief history of the essential eight.
The essential eight was originally developed to promote solid security and operational practices within Australian governmental agencies, departments, local councils, and other businesses in the public sector. Now, many private businesses are now looking at the Essential Eight as a good launching place for measuring security controls and setting a foundation for cyber security. The Australian Cyber Security Centre (ACSC) are the current custodians of the Essential Eight.
When it comes to the security of your business’ information, there are so many factors that come into play; like the sensitivity of your data, or how many employees you have. That’s why there isn’t really a ‘one-size-fits-all’ approach to cyber security – what works for you might be completely disastrous for another business.
A direct quote from the ACSC states:
“while no single mitigation strategy is guaranteed to prevent cyber security incidents, organisations are recommended to implement eight essential mitigation strategies as a baseline. This baseline, known as the essential eight, makes it much harder for adversaries to compromise systems.”
As I mentioned, the ACSC initially created the Essential 8 to mandate information security compliance across governmental branches. While it is not mandatory for most businesses in the private sector, it is still highly recommended. This is because the suggested strategies are a systematic set of security control methods that provide a framework for businesses to manage IT security risks. It’s crucial now more than ever that businesses focus on their information security and protecting their data, and the Essential Eight is built to do just that.
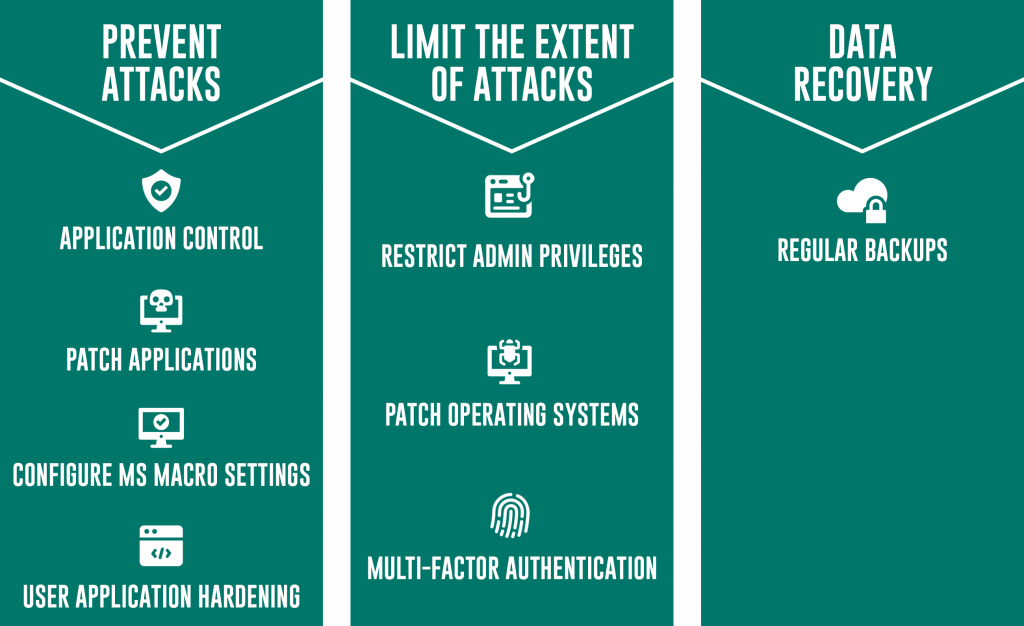
So in short, the essential eight strategies were chosen specifically to fortify the most important avenues of information security, with their main purpose being to protect businesses against malware, ransomware, and data breaches. The strategies are broken up into three components; prevent attacks, limit the extent of attacks, and data availability.
What are the essential eight strategies?
The Essential Eight Maturity Model
Now I’m not going to go into detail about the strategies as we will be discussing them over the next few weeks. What I am going to discuss in this episode is the Essential 8 maturity model.
Before we can get to implementing the Essential 8, the ACSC suggests you first identify a maturity level that is suitable for your organisation. There are currently 4 Maturity levels starting with Maturity Level Zero through to Maturity Level Three.
The maturity levels are focussed on mitigating the increasing levels of a potential adversary’s technique, their tools, their procedures and who they tend to target.
Maturity Level Zero
Let’s start with maturity level zero, which was reintroduced this year. This level signifies that there are weaknesses in an organisations overall cyber security posture. So whether you have none of the strategies in place or if you’ve succeeded in implementing a couple of the strategies, your cyber security maturity will be considered level zero because you have those missing control methods in place that leave you open to attack. Adversaries tend to go for the lowest hanging fruit, so even if you have a really solid backup strategy or you use multi-factor authentication, they can and will find other ways to exploit your system. A lot of businesses will be starting off at level zero, and that’s completely fine because they are attesting to the fact that one or more of their security controls may not be covering their organisation’s cyber risks adequately.
Maturity Level One
Maturity Level One focusses on mitigating the risk of a cyber attack from opportunistic adversaries who are looking for any victim rather than a specific target. For instance, they use normal tools that are available online to identify common exploits or vulnerabilities in software or operating systems that are unpatched. This means you’ll want to mitigate against common threats, and adversaries out there who are opportunistic rather than targeting organisations with any key objectives to get access to specific information. They are still a threat, particularly if they manage to affect the availability of your systems.
Maturity Level Two
The focus of Maturity Level Two is to fight against adversaries who are better equipped and employ more advanced techniques, so they may be specifically targeting your organisation and not just spamming you with phishing emails, and they might attempt to impersonate users or accounts in your organisation to gain privileges and access your data. These adversaries are happy to invest more time into their targets and are often better at bypassing security controls and evading detection. Rather than casting a wide net, they are more selective with who they target, but are also wary about the time, money, and effort they invest to compromise their targets’ systems.
Maturity Level Three
And finally, Maturity Level Three is the highest level, and focusses on deterring adversaries who can exploit opportunities they seek in their targets’ cyber security posture, like old software or inadequate monitoring. They are incredibly knowledgeable and use techniques and tools that are not commonly used by less experienced adversaries. They will make swift use of exploits and will find ways to evade detection and solidify their presence. They focus on very particular targets and are willing to invest a lot of time and effort into completely circumventing all the security controls an organisation may have.
When choosing a maturity level to target, you should consider how desirable your company is to an adversary and the type of information your organisation holds and transmits, so if you house a lot of sensitive or confidential data, you should consider targeting level three. Try to take a risk-based approach to the essential eight and consider the implications and the costs to your business if a data breach or a malware attack were to occur.
Now as a side note, to quote the ACSC again,
“organisations are now advised to achieve a consistent maturity level across all mitigation strategies before moving onto a higher maturity level”.
This is because the essential eight strategies are designed to complement each other and provide a blockade against several threats, so it’s important that you plan your implementation to achieve the same maturity level across all eight strategies before moving onto a higher maturity level.
In this series I’ll be giving you tips on how to reach maturity level one, so hopefully once we’ve finished you’ll have a better understanding of the requirements and will be able to independently reach a higher level if need be.
Do I need to implement the essential eight?
If you’re a governmental department, agency or local council then it will be mandatory to implement the E8 and to have a maturity level rating, so I’d suggest you have your E8 implementation assessed by a third party or by your MSP.
If you’re a small to medium sized business, or even a larger organisation who hasn’t begun their journey into cyber security, then I would still suggest you implement the strategies to the best of your ability so you have a maturity level that sets a foundation for further cyber security control.
- Mandatory for governmental agencies and departments.
- Not mandatory for most businesses in the private sector.
You don’t have to get your implementation assessed by a third party of course, but I’d still suggest you do because if you’re going to go to all the trouble to implement the E8 you should make sure you’ve done it correctly.
And that’s it for this episode! If you have any questions about the maturity models please feel free to contact us, and I’ll see you next week for episode 2!